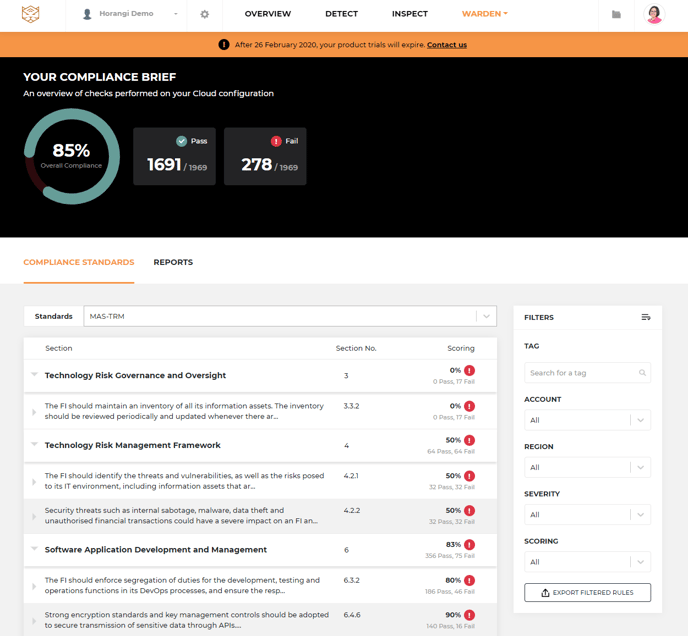
The Compliance Standards view helps you get a big picture of your overall compliance to a particular standard without having to generate a report every time.
Why Compliance?
With more organizations migrating to cloud infrastructure, the risk landscape for infrastructure and security teams is changing. Making sure that organizations comply with governing laws and regulations is one of the biggest challenges in cloud security.
It’s no secret that the cost of non-compliance is extremely high. Here at Horangi, we believe in being proactive about managing compliance instead of scrambling when it’s too late.
Warden's Compliance feature makes becoming and staying compliant easier, from a bird's eye view to the technical details, it simplifies the compliance workflows between your DevOps, Security and Compliance teams.
Compliance Standards
- Compliance Tagging: To quickly filter through your findings and focus on the compliance standard that matters to you, findings have been tagged to the following standards that they relate to.
- Control-Level Mapping: Horangi has mapped findings to the individual control items that they relate to for standards that have them.
|
Compliance Standard |
Tag |
Description |
Compliance Tagging |
Control Mapping |
|
Center of Internet Security (CIS) Benchmarks
|
CIS-AWS, CIS-GCP |
A set of open source, consensus-based guidelines that provide a baseline for assessing your security. |
|
|
|
Monetary Authority of Singapore's Technology Risk Management (MAS-TRM) |
MAS-TRM |
A set of guidelines, based on the public consultation paper dating from 2019. |
|
|
|
MAS Cyber Hygiene Notices |
MAS-CYBER-HYGIENE |
A legally binding subset of MAS-TRM targeting specific industries. |
|
|
|
Payment Card Industry Data Security Standard (PCI DSS) |
PCI-DSS |
A security standard for organizations that handle credit cards from major card schemes. |
|
|
|
National Institute of Standards and Technology (NIST) Cybersecurity Framework |
NIST |
Guidelines for US-based organizations in securing data and infrastructure. |
|
|
|
AWS Well-Architected Framework (AWS-WAF)
|
AWS-WAF |
A framework to help cloud architects secure their AWS infrastructure based on best practices. |
|
|
|
Bank Negara Malaysia - Risk Management in Technology (BNM-RMiT) |
BNM-RMIT |
A set of legally binding standards aimed to make financial institutions operating in Malaysia resilient to cybersecurity threats. |
|
|
|
International Standards Organization 27001 (ISO 27001) |
ISO27001 |
A standard providing the requirements for an information security management system (ISMS). |
|
|
|
Australian Prudential Regulation Authority (APRA) Prudential Practice Guide CPG 234 |
APRA |
A guide that identifies Information Security weaknesses within Australian financial institutions. |
|
|
Parts of Compliance Standards View
Compliance Brief
An overview of your overall compliance risk posture.
Compliance Standards Tab
1. Section: Compliance control items are grouped by the section of the compliance standard that they belong to.
2. Section Number: The number (or identifier) of the section or control item as per the compliance standard's documentation.
3. Scoring: Scoring displays whether a Warden rule checking for a misconfiguration has passed or failed a check on a resource.
Navigating Compliance Standards View
- Select a compliance standard in the Standards dropdown list.
- View a list of all the compliance controls the rules map to and your compliance scoring for that control.
- Click on the compliance control you want to drill down into. You can then see the rules that are associated with your compliance to that control.