What is Terraform?
Terraform is an Open Source Infrastructure-As-Code software tool. Users can define infrastructure requirements using a declarative configuration language, such as JSON.
What are Terraform Remediations?
Here at Horangi, we created Terraform Remediations for users who are currently using Terraform for their Cloud Infrastructure. For supported rules, Horangi will display an example Terraform code snippet. Based on the example, users can make the same changes into their own Terraform templates to help comply with Horangi rules. This allows users to fix these vulnerabilities at build time.
The example Terraform code snippet is an example only and does not reflect the complete state of the user’s cloud resource. As you will see, Horangi will highlight which part of your Terraform code needs to be changed in order to remediate your environment configurations.
Finding the remediation steps
-
Log into your Horangi Storyfier account.
-
At the top navigation bar, click on RULES.

-
Look for the rule where you would like to perform Terraform remediations on. For this document, we will be using the SNS Topic Server-Side Encryption Not Enabled Rule as an example.
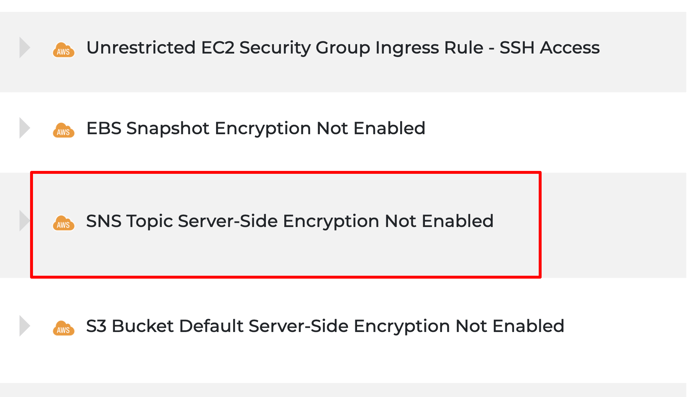
-
Click on the rule to expand it and select the appropriate account. Next, select the appropriate resource.
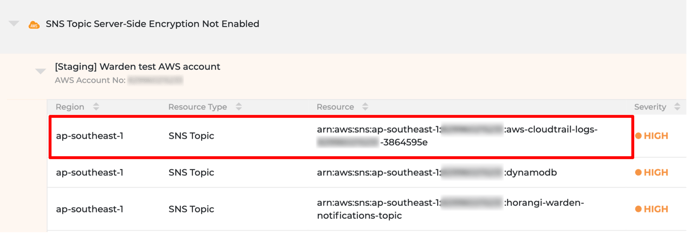
-
On the right window, click on the Remediation tab, followed by Terraform.
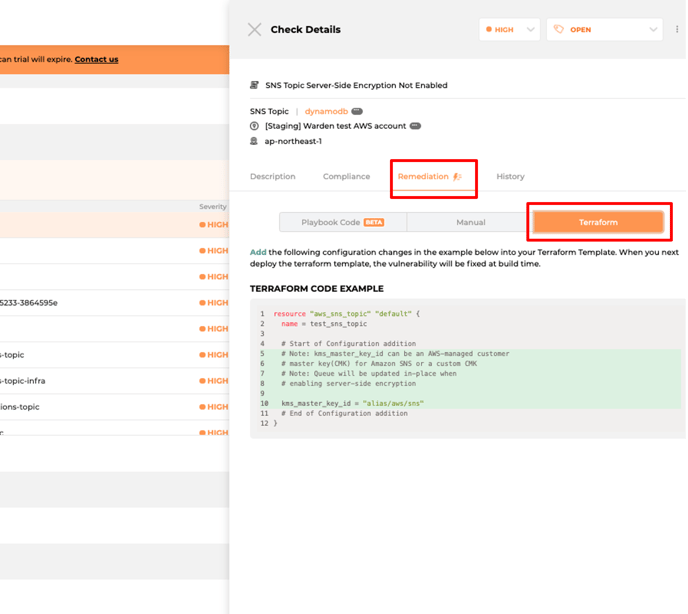
-
You will find the required Terraform code to change, highlighted in either green or red.
Terraform Remediation Types
There are two types of Terraform remediations.
- Addition to Terraform Resource
- Modification to Terraform Resource
Addition to Terraform Resource
This involves adding arguments to existing Terraform resources.
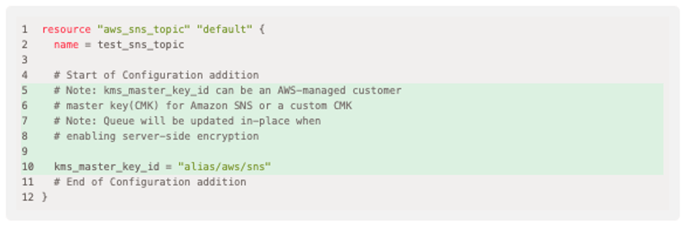
In the example above, the template shows the arguments to add (highlighted in green) in your own Terraform template.
Modification to Terraform Resource
This involves modifying or removing arguments from existing Terraform resources.
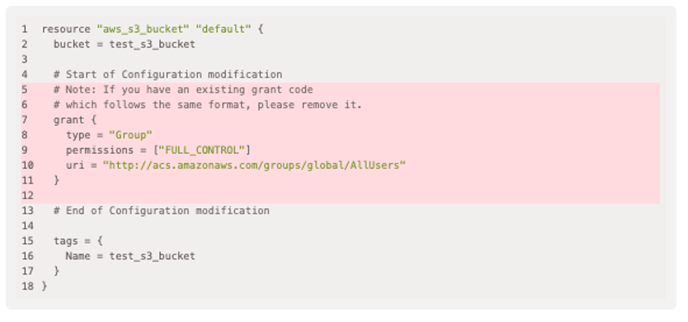
In the example above, the template shows which arguments to remove or modify (highlighted in red) in your own Terraform template.
Terraform Remediation Requirements
- You must have used Terraform to create your Cloud resources
- Resources created using the CLI or Console will not be able to use Terraform remediations
Rule Support
The following rules currently support Terraform Remediations:
- AWS
- ALB Access Activity Logging Not Enabled
- ALB (ELBv2) Security Policy Not Secure
- ElastiCache At-Rest Encryption Not Enabled
- ElastiCache In-Transit Encryption Not Enabled
- ElasticSearch At-Rest Encryption Not Enabled
- ElasticSearch Node-To-Node Encryption Not Enabled
- ELB Access Activity Logging Not Enabled
- ELBv2 Deletion Protection Not Enabled
- Kinesis At-Rest Encryption Not Enabled
- NLB (ELBv2) Security Policy Not Secure
- RDS Deletion Protection Not Enabled
- RDS Instance Encryption Not Enabled
- S3 Default Encryption Not Enabled
- S3 Bucket Not Configured with Public Access Block
- S3 Bucket with Authenticated Full Control Permission
- S3 Bucket with Authenticated Read ACP Permission
- S3 Bucket with Authenticated Read Permission
- S3 Bucket with Authenticated Write ACP Permission
- S3 Bucket with Authenticated Write Permission
- S3 Bucket with Public Full Control Permission
- S3 Bucket with Public Read ACP Permission
- S3 Bucket with Public Read Permission
- S3 Bucket with Public Write ACP Permission
- S3 Bucket with Public Write Permissions
- SNS Server-Side Encryption Not Enabled
- SQS Server-Side Encryption Not Enabled
