AWS S3 Bucket Log Connector Prerequisite Infrastructure
Before you can set up Warden Threat Detection in your AWS environment, there has to be a logging infrastructure in place. This document covers the required infrastructure you need to set up Warden Threat Detection for AWS.
Pre-Requisites
- An AWS CloudTrail Trail.
- An AWS S3 bucket that receives logs from the trail.
- SSE-KMS encrypted SNS Topic configured to receive event notifications from the same S3 Bucket.
If you have an organization-wide CloudTrail, Warden Threat Detection will process events from your AWS Organization. Otherwise, only events from CloudTrail’s AWS Account will be processed.
Reference Deployment Architecture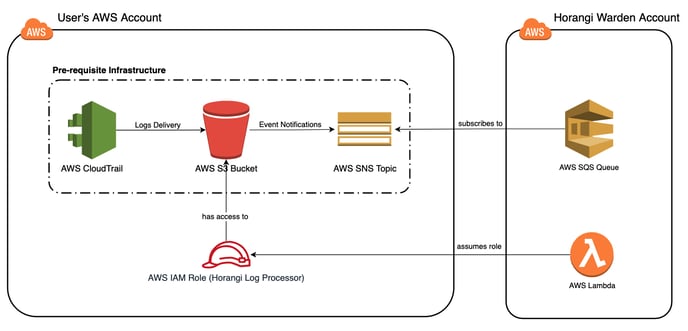
You can see step by step guide on the onboarding page in Warden. Click here to start Log Integration in Warden.
You can also check out the details below.
Setting Up the Log Ingestion Stack
Based on your current AWS Cloud Infrastructure, you may fall into one of the following scenarios:
- Scenario 1: No CloudTrail, no S3 Bucket and no SNS Topic
- Scenario 2: Existing CloudTrail with logs delivered to an S3 Bucket, no KMS Key and/or S3 Bucket nor SSE-KMS encrypted, and no SSE-KMS encrypted SNS Topic configured to receive event notifications from the S3 Bucket
- Scenario 3: Existing CloudTrail with logs delivered to an S3 Bucket, an SSE-KMS encrypted SNS Topic configured to receive event notifications from the same S3 Bucket, and S3 Bucket and SNS Topic encrypted with the same KMS Key
Scenario 1: No CloudTrail, no S3 Bucket and no SNS Topic
1. Log in to the AWS Account where you would like to set up threat detection.
2. Click on this Warden Log Processing Infrastructure CloudFormation Template which automatically sets up the Stack parameters for you. You can review our CloudFormation template here.
3. Click Create Stack.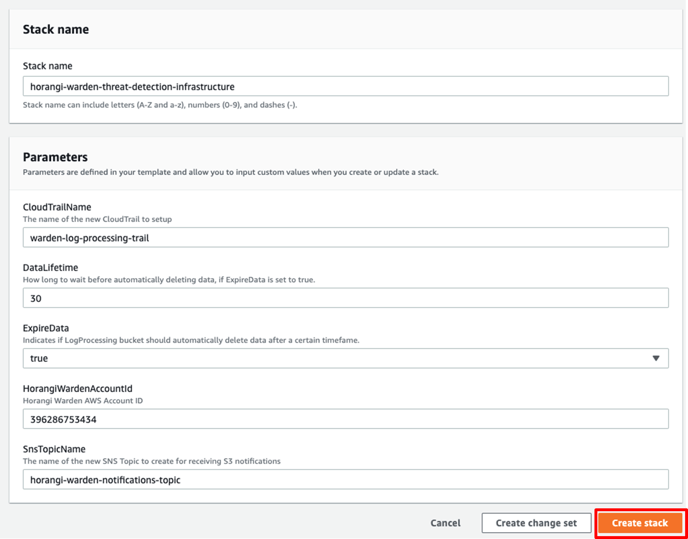
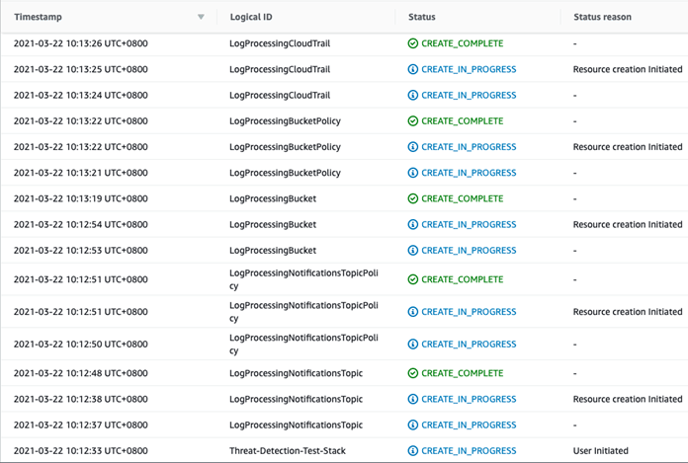
4. CloudFormation will automatically create the resources needed in your account. You should then see all the resources created in the Events tab.
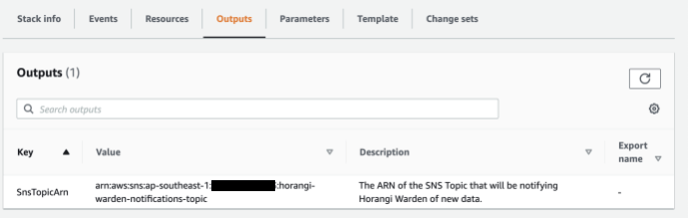
5. Take note of the fields in the Outputs tab. They will be used as inputs when adding a new AWS S3 Bucket Logs Connector in Storyfier.
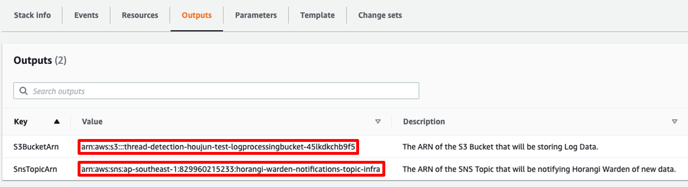
Scenario 2:
- Existing CloudTrail with logs delivered to an S3 Bucket
- No KMS Key and/or S3 Bucket not SSE-KMS encrypted
- No SSE-KMS encrypted SNS Topic configured to receive event notifications from the S3 Bucket
1. Log in to the AWS Account where you would like to set up threat detection.
2. Click on this Warden Log Processing Notifications CloudFormation Template which automatically sets up the Stack parameters for you. You can review our CloudFormation template here.
3. Click Create Stack.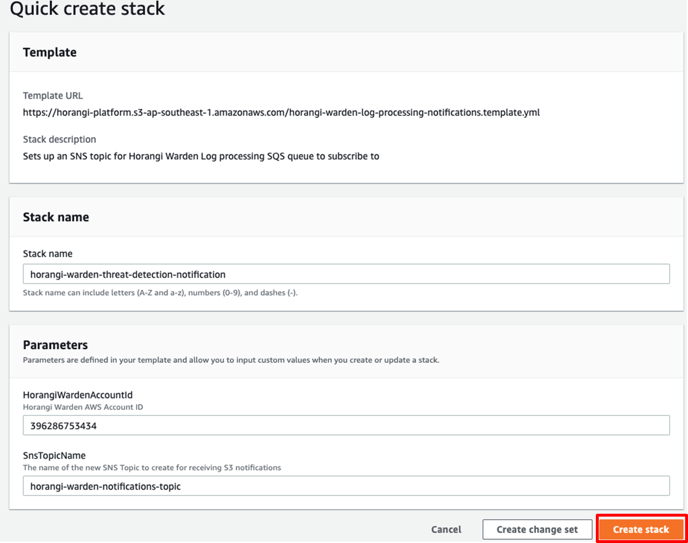
4. CloudFormation will automatically create the resources needed to ensure threat detection in your account. You should then see all the resources created in the Events tab.
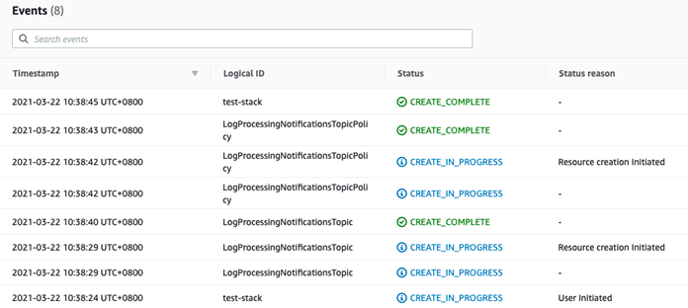
5. Take note of the field in the Outputs tab. It will be used as an input when adding a new AWS S3 Bucket Logs Connector in Storyfier.
6. Navigate to the S3 console at https://console.aws.amazon.com/s3.
7. Select the S3 bucket that will receive all CloudTrail Logs and go to the Properties tab.
8. Go to Default encryption, and select edit.
9. Set the Server-side encryption to Enable. The Encryption key typeshould be set to AWS Key Management Service key (SSE-KMS). The AWS KMS key field, select Choose from your AWS KMS keys and select the KMS key ARN that was created in the stack above. Set Bucket Key to Enable, then Save changes.
10. Click Event Notifications and select Create event notification.
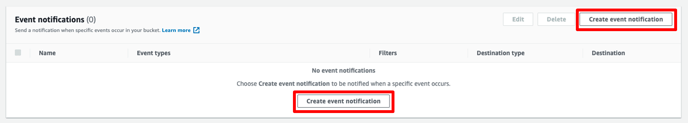
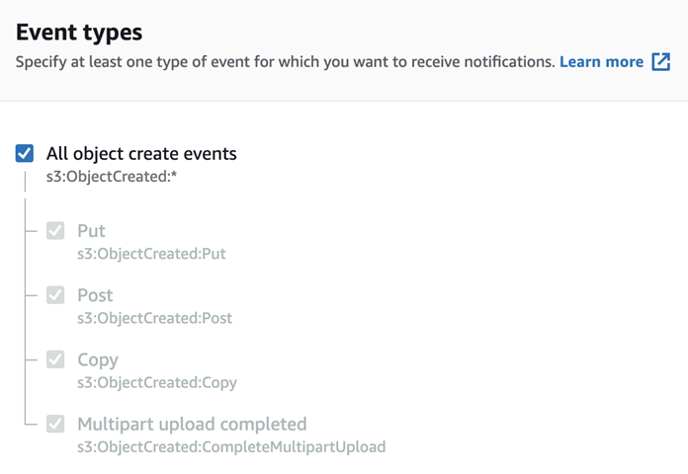
11. Enter your desired Event name, and under Event Types, select All object create events.
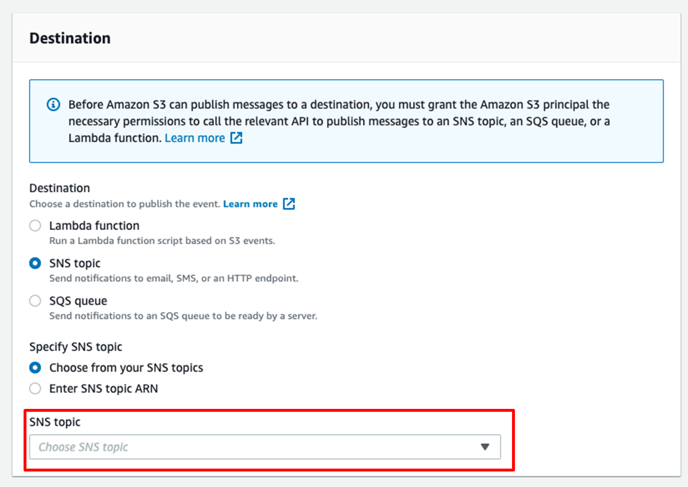
12. Under Destinations, select SNS topic, and choose the SNS topic name created in Step 5.
Scenario 3:
- Existing CloudTrail with logs delivered to an S3 Bucket
- SSE-KMS encrypted SNS Topic configured to receive event notifications from the same S3 Bucket
- S3 Bucket and SNS Topic encrypted with the same KMS Key
Set up and configure notifications so that key events on buckets cause a message to be sent to an Amazon SNS topic.
1. Log in to the AWS Account where you would like to set up threat detection.
2. Navigate to the AWS Simple Notification Console and select the Topic you created for threat detection.
3. On the top right corner, select Edit.
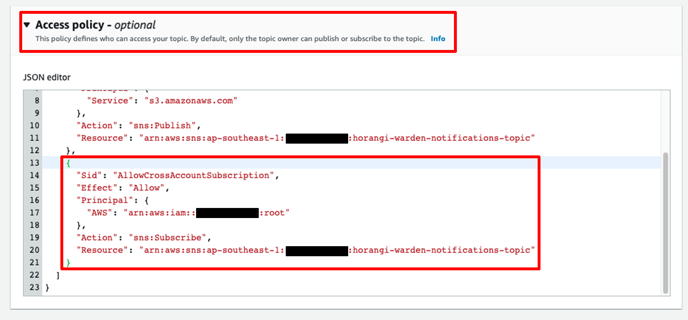
4. Scroll to the Access Policy box, expand it and add on the code below.
{
"Sid": "AllowCrossAccountSubscriptionForWardenThreatDetection",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::396286753434:root"
},
"Action": "sns:Subscribe",
"Resource": "arn:aws:sns:<your_region>:<your_aws_account_id>:<your_sns_topic_name>"
}
5. Scroll down and click Save changes.
6. Navigate to the S3 console at https://console.aws.amazon.com/s3.
7. Select the S3 bucket that will receive all CloudTrail Logs and go to the Properties tab.

8. Navigate to Event Notifications and select Create event notification.

9. Enter your desired Event name, and under Event Types, select All object create events.

10. Under Destinations, select SNS topic, and choose the name of the SNS topic that we configured in Step 4.
11. Next, after finishing all prerequisites, log in to Warden to set up Threat Detection Integration. Continue to see How to set up Threat Detection Integration in Warden.
Click here to log in to Warden to start setting up Threat Detection Integration.