This document helps you to onboard Threat Detection on your cloud environment.
- Log into your Horangi Storyfier platform - Warden.
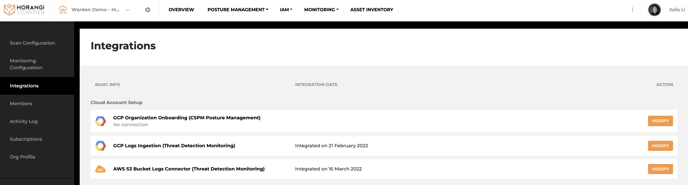
- Click on the gear icon at the top left. On the left panel, click on Integrations.
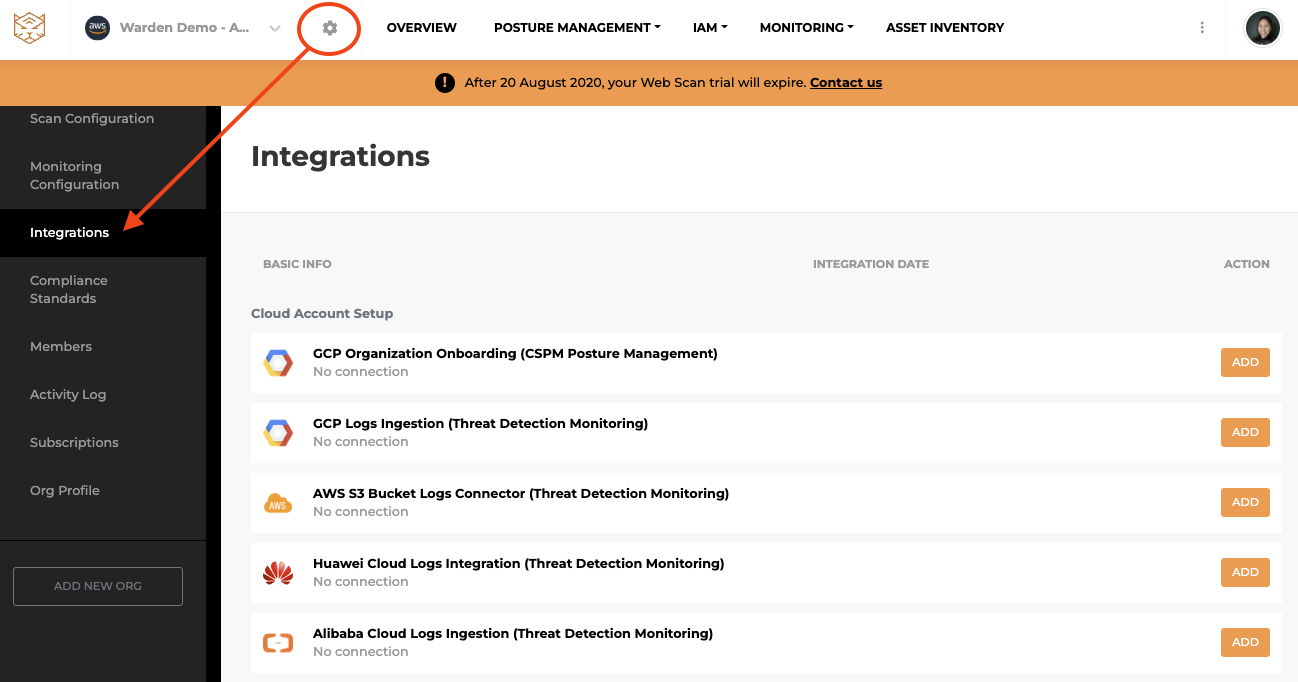
-
Add AWS S3 Bucket Logs Connector
-
Add GCP Logs Ingestion
-
Add Huawei Cloud Logs Integration
-
Add Alibaba Cloud Logs Integration
Add AWS S3 Bucket Logs Connector
- On the Integrations page, look for the AWS S3 Bucket Logs Connector row and click ADD.

- Click ADD NEW S3 BUCKET LOGS CONNECTOR
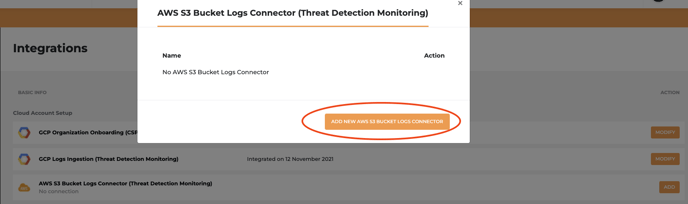
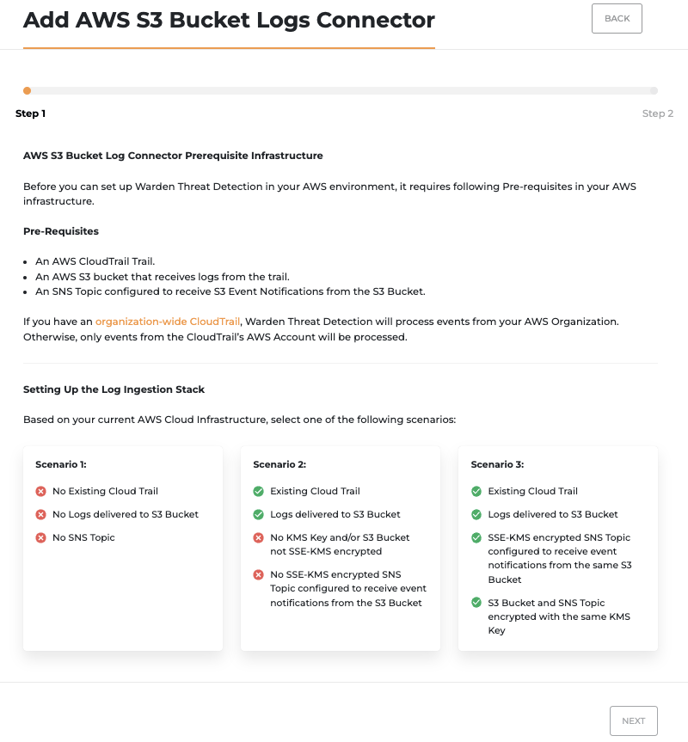
- Next, choose a scenario based on your current infrastructure and click NEXT to see step by step guide for all necessary setup. (click here to preview step by step guide for each scenario on how to set up your prerequisite AWS infrastructure)
- Next, fill up the details of your S3 Bucket.
- Name - Name of your integration
- Account ID - 12 Digit AWS Account ID where S3 bucket that receives cloudtrail logs is located
- Bucket Name - S3 Bucket where CloudTrail Logs and other log types are delivered
- KMS Key - provide KMS Key ARN
- SNS Topic ARN - SNS Topic used to retrieve S3 Event Notifications from.
- After filling up the necessary information, next, we are creating an IAM Role to allow Horangi Access into your S3 Bucket with CloudFormation.
- Click on the LAUNCH CLOUDFORMATION STACK button. You can review our CloudFormation template here.
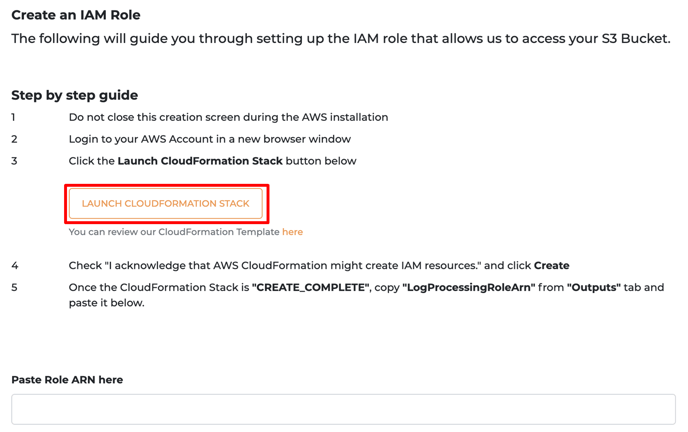
- After reviewing all the parameters, check the “I acknowledge that AWS CloudFormation might create IAM resources” box.
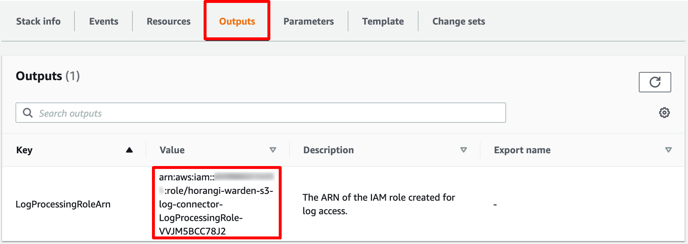
- Go to the Output tab and get the LogProcessingRoleArn field and paste it in Step 2 of the AWS S3 Log Connector.
- Once the connection is successful, you will be able to view your integration on the Integrations page.
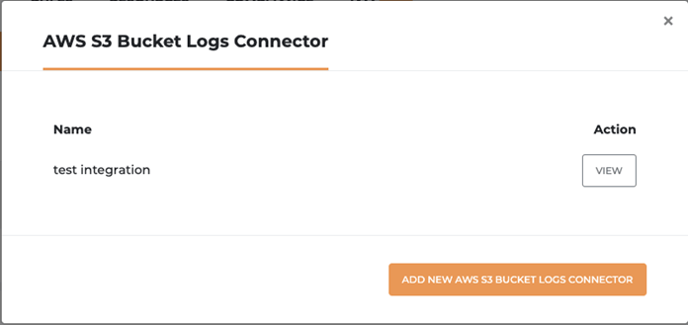
Now, click here to go to Warden to set up Threat Detection Integration.
Add GCP Logs Ingestion
- On the Integrations page, look for the GCP Logs Ingestion and click ADD
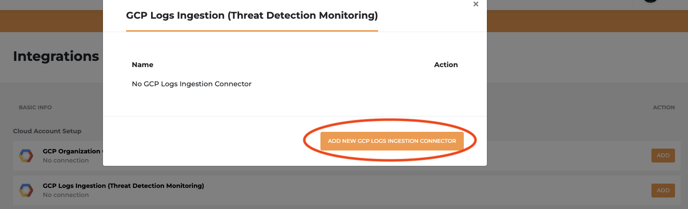
- Click ADD NEW GCP LOGS INGESTION CONNECTOR
- Next, follow step by step guide on the onboarding page to create a service account and a Pub/Sub Topic for integration. (click here to preview step by step guide)
- Fill up the details of your Google Cloud information for integration.
- Google Cloud Organization Name - Name of your integration
- Project ID - Project id in your Google Cloud Platform
- Topic ID - horangi-warden-gcp-logs-integration-topic that you created in the Pub/Sub for this Integration.
- Subscription ID - horangi-warden-gcp-logs-integration-subscription that you created in the Pub/Sub Subscription for this Integration.
- API Credentials
- After filling up the necessary information, click ADD to finish the integration. Once the connection is successful, you will be able to view your integration on the Integrations page.
Now, click here to go to Warden to set up Threat Detection Integration.
Add Huawei Cloud Logs Integration
- On the Integrations page, look for the Huawei Cloud Logs Integration and click ADD
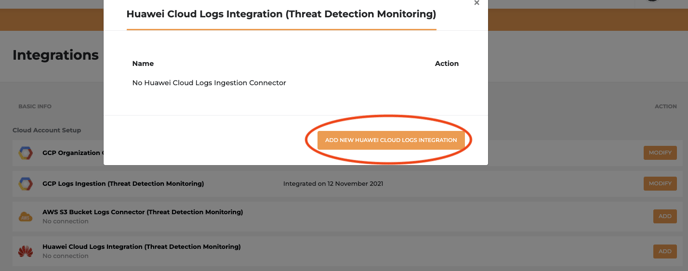
- Click ADD NEW HUAWEI CLOUD LOGS INTEGRATION
- Next, follow step by step guide on the onboarding page. (click here to preview step by step guide)
- Fill up the details of your Huawei Cloud information created for integration.
- Region field should be the region where you would like to enable the CTS log ingestion and create the cloud resources related to this onboarding.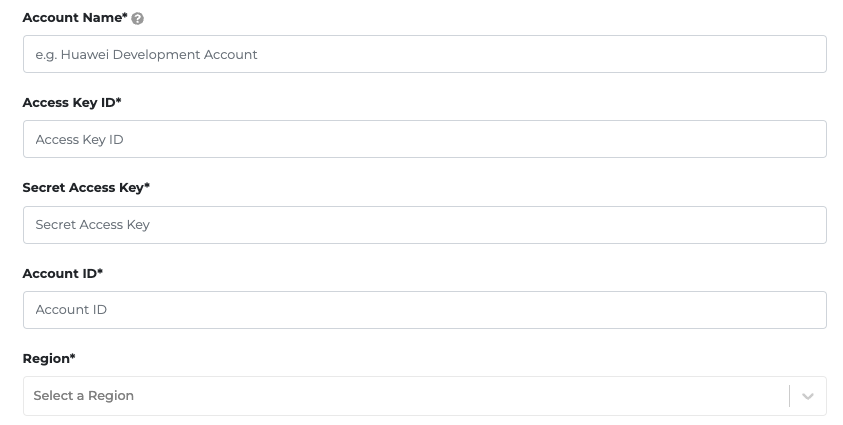
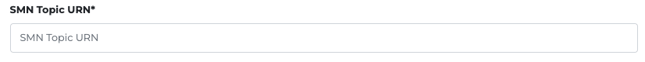
- After filling up the necessary information, click COMPLETE to finish the integration. Once the connection is successful, you will be able to view your integration on the Integrations page.
Now, click here to go to Warden to set up Threat Detection Integration.
Add Alibaba Cloud Logs Integration
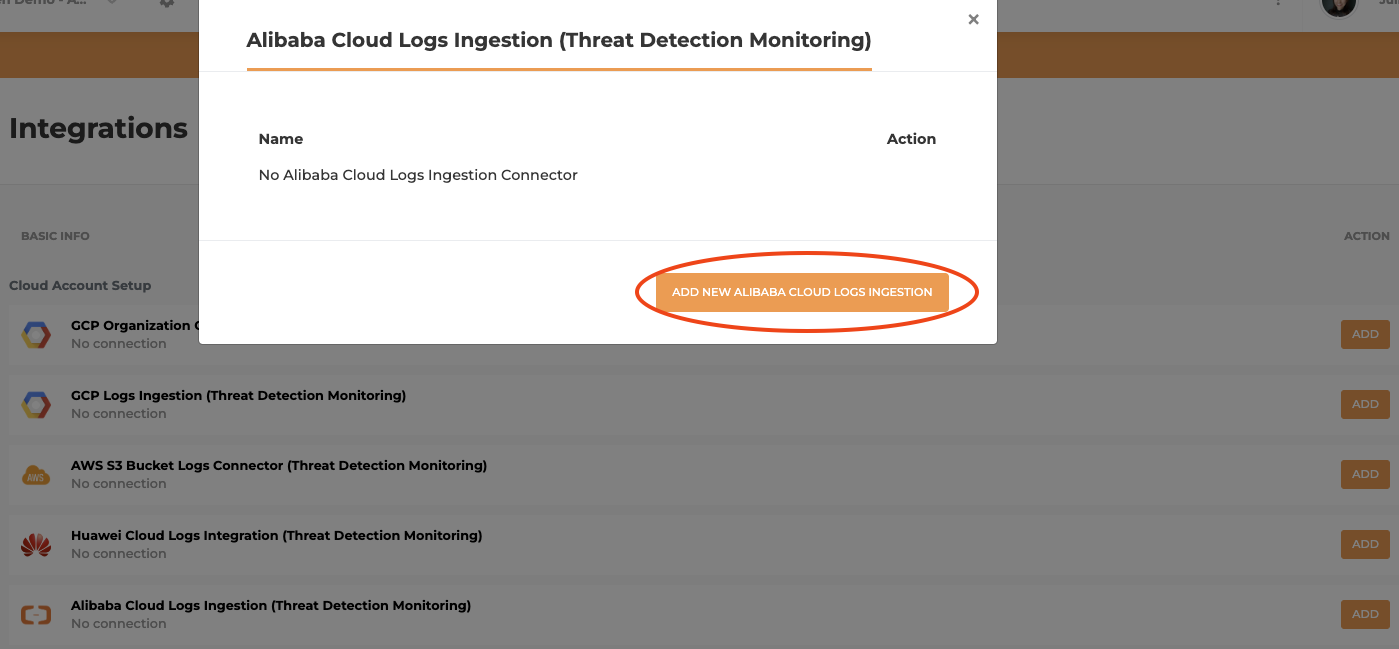
- On the Integrations page, look for the Alibaba Cloud Logs Integration and click ADD

- Click ADD NEW ALIBABA CLOUD LOGS INTEGRATION
- Next, follow step by step guide on the onboarding page. (click here to preview step by step guide)
- Fill up the details of your Alibaba Cloud information created for integration.

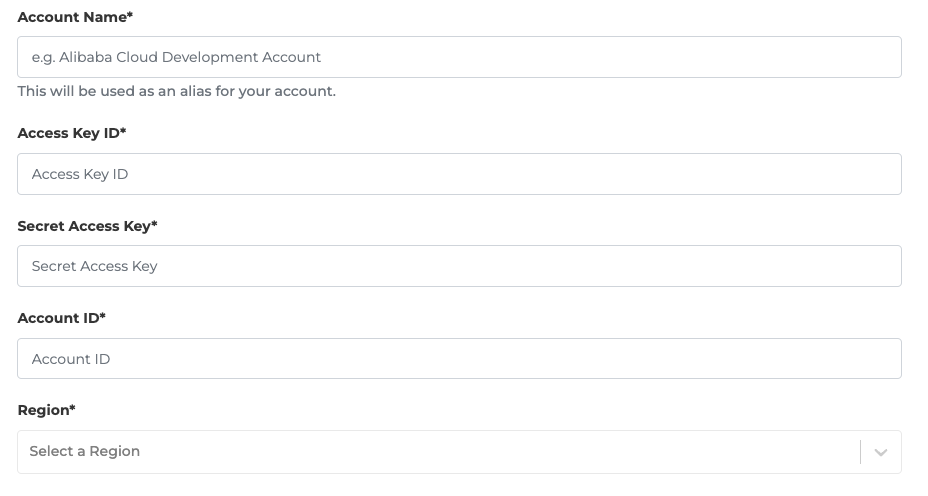
- After filling up the necessary information, click COMPLETE to finish the integration. Once the connection is successful, you will be able to view your integration on the Integrations page.
Now, click here to go to Warden to set up Threat Detection Integration.
Offboarding
When you offboard threat detection from your AWS environment, Warden will stop receiving events from the particular S3 bucket.
To offboard threat detection from your AWS environment, you will need to remove the S3 Log Connector from your Horangi account.
- Log into your Horangi Storyfier platform.
- Click on the gear icon at the top left. On the left panel, click on Integrations. Look for the AWS S3 Bucket Logs Connector row and click ADD.


- Select the View button for the S3 Bucket Log Connector that you want to offboard.

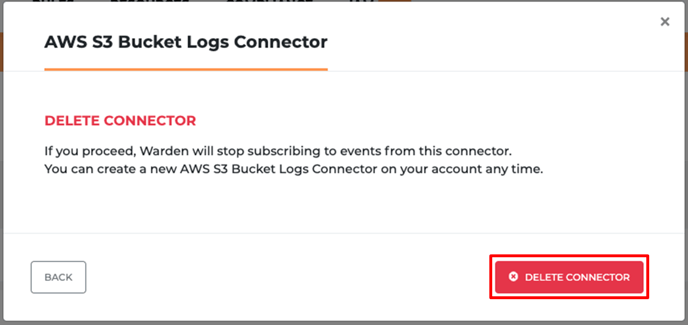
- Now, click on the DELETE CONNECTION button on the bottom left.
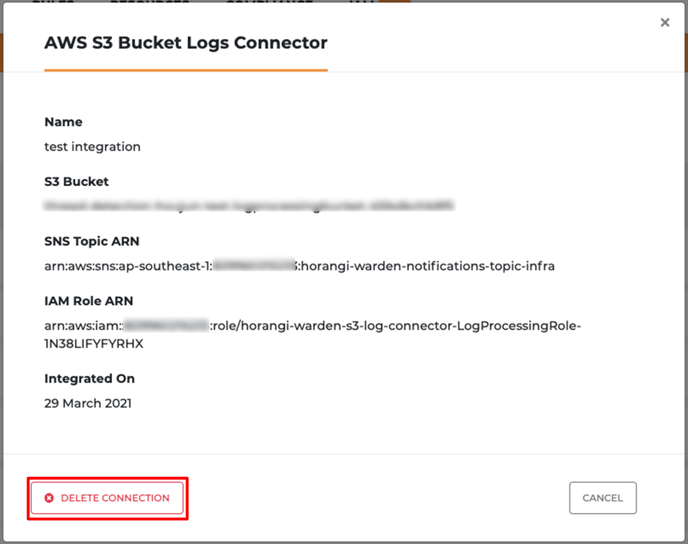
- After clicking DELETE CONNECTION, select DELETE CONNECTOR in the next pop-up window.