Before you can set up Warden Threat Detection in your Huawei Cloud environment, there has to be a logging infrastructure in place. This document covers the required infrastructure you need to set up for Warden Threat Detection Integration.
You can also see the same step by step guide on the integration page in Warden. Click here to log in to Warden to start integration.
Step by Step Guide
- Login to your Huawei Cloud console.
- Create an IAM Custom Policy. Navigate to the IAM permissions page under the IAM service.
- Click on Create Custom Policy to create the SMN-related policy.
- Give an appropriate name (i.e, WardenLogIngestionSMNPolicy) for Policy Name.
- Select JSON under Policy View.
- Copy the following text from the JSON here into the Policy Content field.
- Click OK.
- Create an IAM User Group - navigate to the User Groups page under IAM service.
- Click on Create User Group.
- Give an appropriate name (i.e, WardenLogIngestionGroup).
- Click OK.
- Click Authorize on the created user group.
- Find and select the Custom Policies created in step 2.
- Click Next, OK then Finish.
- Create an IAM User - navigate to the IAM Users page under IAM service.
- Click on Create User.
- Give an appropriate name (i.e, WardenLogIngestionSystemUser) for the username.
- Select only Programmatic Access under Access Type.
- Select only Access key under Credential Type.
- Click Next
- Select the User Group created in step 3.
- Click Create User.
- Click Download Access Key.
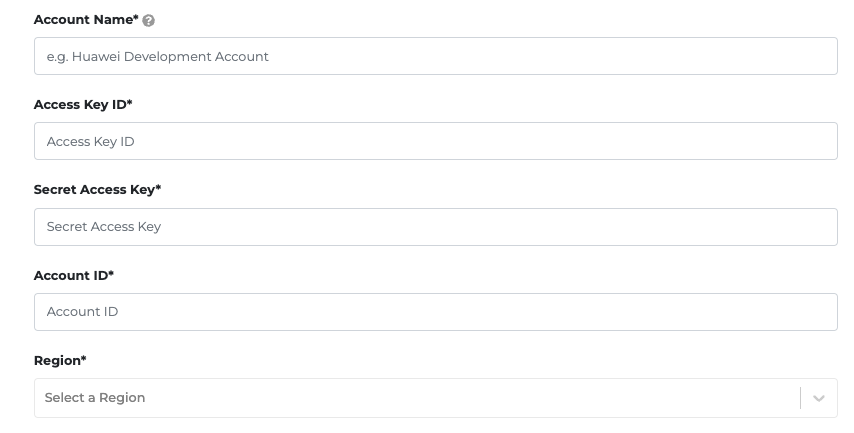
- Copy the Access Key Id and the Secret Access Key from the downloaded file and paste it onto the corresponding fields.
- Copy the Account ID into the field.
- To find the Account ID, hover over your username on the upper right of the page and click on the My Credentials link. You can also access the page here.
- Look for the Account ID field.
- The Region field should be the region where you would like to enable the CTS log ingestion and creating the cloud resources related to this onboarding.
- Create an SMN Topic - navigate to Topic Management then Topics page under SMN service.
- Click on Create Topic.
- Give an appropriate name (i.e. WardenLogIngestionTopic) for the topic name.
- Select the desired Enterprise project (default).
- Click OK.
- Click More on the created topic then click Configure Topic Policy.
- Select All users on the users who can publish to the created topic.
- Check OBS on the services allowed to publish on the created topic.
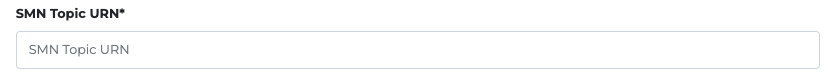
- Hover on the URN of the created topic.
- Copy the SMN Topic URN and paste it in the SMN Topic field.
- Navigate to the Cloud Trace Service page.
- Select the region where you would like to have the threat detection integration.
- Enable CTS if it's not yet enabled by clicking Enable and Authorize.
- In the CTS, navigate to Key Event Notifications.
- Click on Create Key Event Notification.
- Enter a name for the Key Event Notification (i.e. WardenLogIngestionNotification).
- In the Topic section, select Yes.
- Select the previously created SMN Topic in the dropdown list that appears.
- Click OK.
Continue to see How to set up Threat Detection Integration in Warden.
