After you are done with the onboarding procedure here, a default monitoring group is automatically set up for monitoring all Critical to Low severity changes in your infrastructure.
Overview of Monitoring Groups
Monitoring group configuration will allow you to finely configure monitoring in Warden so that you can reduce noise and only receive alerts for the types of changes and threats that matter to your specific use cases and business. You can create multiple monitoring groups to monitor different types of alerts.
What you can configure:
1. Notification configuration
You will be able to enable/disable receiving of the alerts through your notification channels (currently supporting Slack).
2. Scope of the monitoring group
Include/Exclude - Provider, Account, Region, User, IP Address, Resource Type & Id
You can limit the scope being monitored to a specific account, cloud provider or region so that alerts are only triggered on those conditions. This allows you to create different monitoring groups for different environments you want to monitor separately.
You can also exclude specific trusted users from the monitoring group, in which case all the activities from those users will be suppressed by default.
For example, Monitoring only for a production environment, Monitoring activities outside of the Singapore region, Monitoring exclude CI/CD users.
3. Rule configuration
Configure which alerts will be triggered for this monitoring group, for example:
- You can turn off the rules that have lower severity so that you can only focus on high and critical alerts. You will then no longer get alerts from these rules for this monitoring group.
- You can change the severity of each rule for each monitoring group based on your organization’s standards.
4. Multiple monitoring groups based on different teams’ needs
For example, Engineering leads want to be notified when there are high-risk infrastructure changes, while security teams want to focus on anomaly behaviours or cyber-attacks. Please refer to the examples below.
Configuring Monitoring Groups
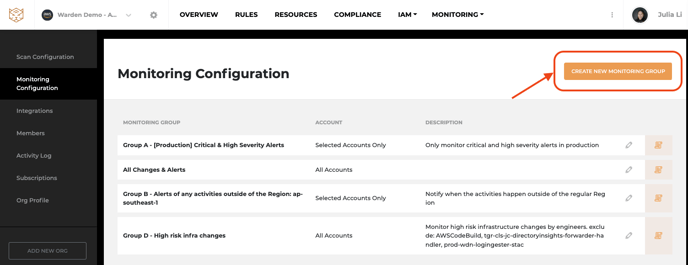
Add a new monitoring group
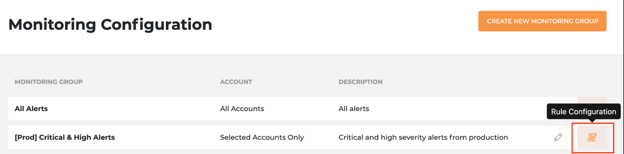
Step 1: On the Monitoring Alerts page, click [Monitoring Configuration] on the right up corner to go to the monitoring configuration page.

Step2: Click [CREATE NEW MONITORING GROUP] to open the new Monitoring Group configuration page.
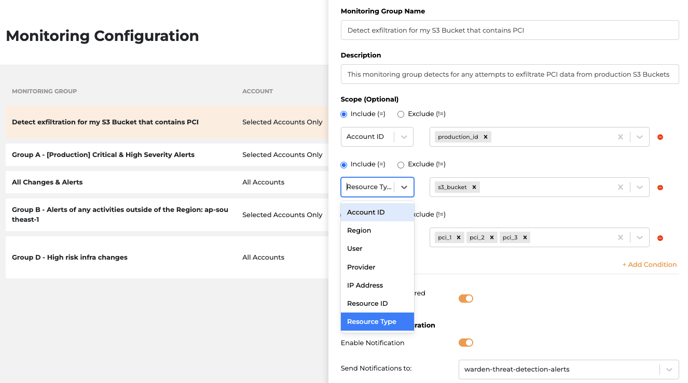
 Step 3: Configure your monitoring group details
Step 3: Configure your monitoring group details
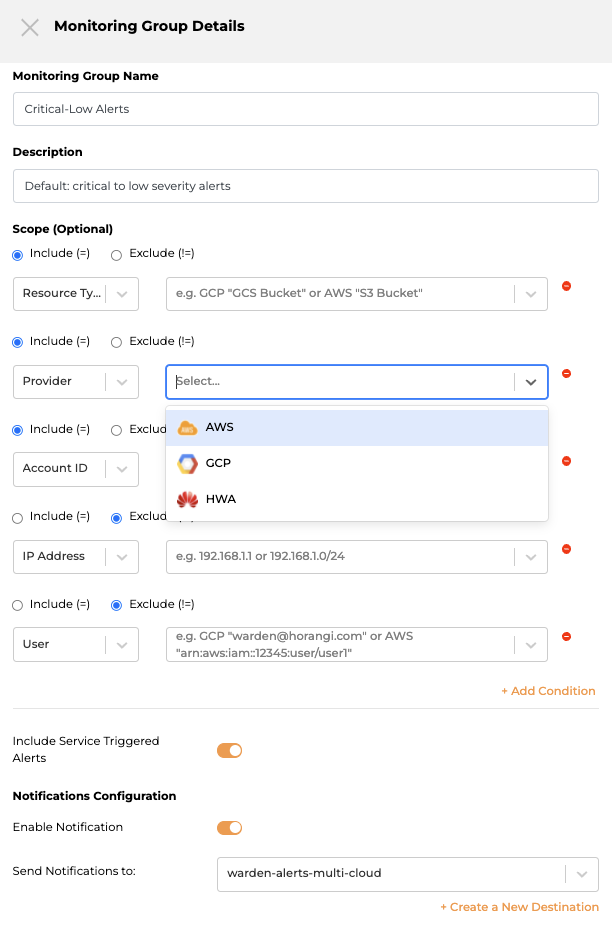
- Define the monitoring group name for easy identification. (this will be displayed in alerts and filters).
Example:
-
- All-alerts
- [Production]- Critical & High Severity Alerts
- [Production]-High-risk infra changes
- [Non-Singapore] All Activities
Scope Configuration
- Add scope conditions: These are filters on what is being monitored in this group and allow users to restrict monitoring (and the alerts that will be generated) to a defined scope: currently supports including or excluding certain Account ID, Region, Provider, IP addresses, User and Resources.
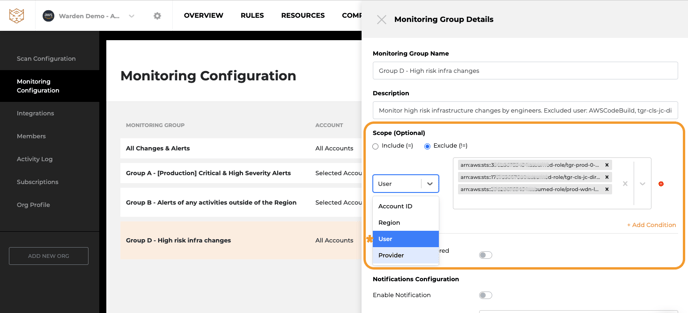
- Include Service Triggered Alerts: Enabling this setting will include all alerts triggered by either the cloud provider (ie auto-scaling) in addition to those triggered directly by actual users. You can cut noise by disabling it if you only care about user-triggered alerts.
Notification Configuration
 Enable the notification and add a new slack channel to get notified immediately.
Enable the notification and add a new slack channel to get notified immediately.
If you disable the notification, you will not receive slack notifications, but you can still see the alerts on the Monitoring - Alerts page.
Slack notification example:
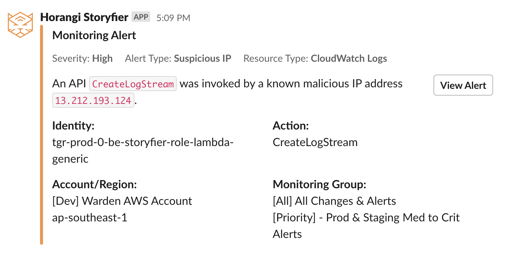
If your slack account has not been integrated to Warden yet, please go to integrations to connect your slack account. Read more.
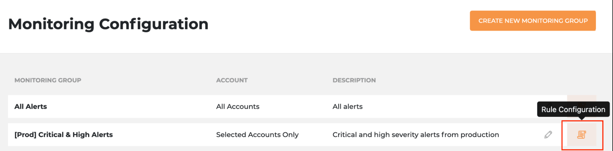
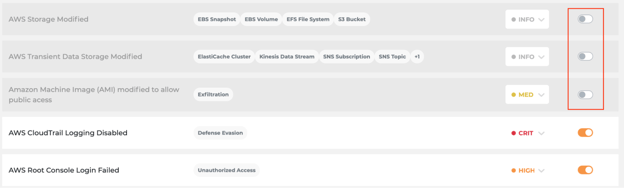
Rule Configuration
- Click the
to open the list of rules that can generate alerts
- You can set the pre-defined severity and status of each rule for the current monitoring group.
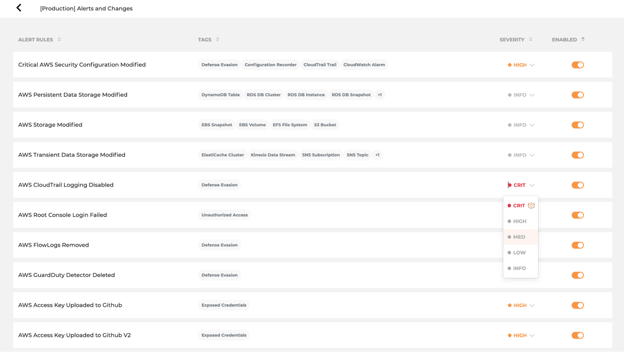
- Turn off the alerts for rules that are not relevant to your business.
After you have done all of the above, you will start receiving alerts based on your configured monitoring group.
Examples
Monitoring Group Configuration Example 1:
Get notification of critical and high severity alerts only for the production environment
Here is an example for monitoring group configuration.
- You want all alerts to be shown on the monitoring alerts page, but don’t want to get the slack notification for each alert.
- You want to get notified immediately via slack channel only for the higher risk alerts from the production environment.
In this case, we can create two monitoring groups.
-
- All Alerts
- [Priority] - Prod & Staging Med to Crit Alerts
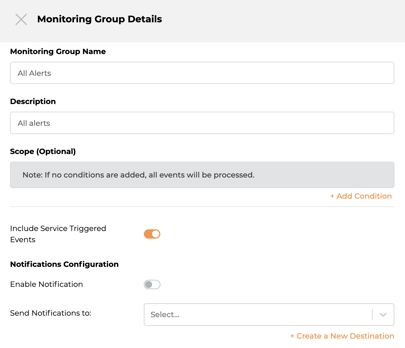
Monitoring Group 1 - All Alerts: Create a monitoring group with the default configuration.
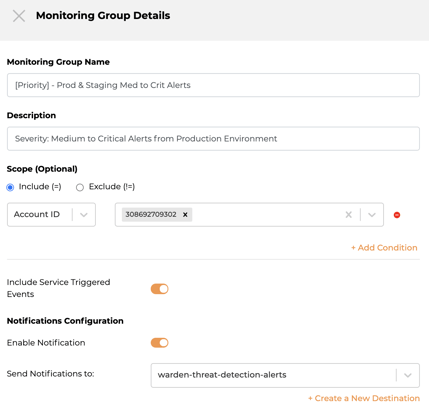
Monitoring Group 2 - [Priority] - Prod & Staging Med to Crit Alerts:
1) Create a monitoring group- Scope: Add condition, select Include(=), select ‘Account ID’ = {production account ID}
- Enable ‘Include Service Triggered Events’
- Notifications Configuration: Enable Notification, Send Notifications to: {your slack channel name: warden-threat-detection-alerts}
(Create a new slack channel here directly if you need a new channel for the alerts.)
Turn off all the rules with severity ‘INFO’, ‘LOW’, ‘MED’, and only keep the rules with critical and high severity remain enabled.

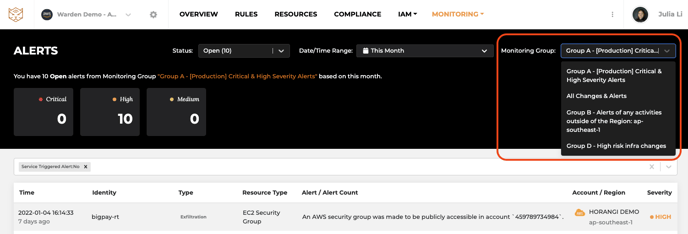
All done! Now let’s see how it works in real alerts.
- Monitoring - Alerts

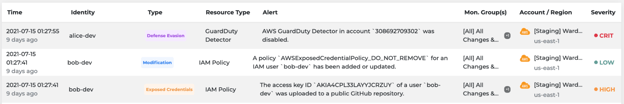
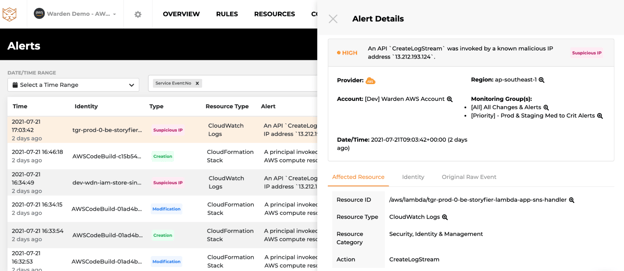
- Slack Notifications

- Alert Details
Example 2:
Get separate alerts for different cloud regions
If your organization is managing the environment by different cloud regions or has different monitoring thresholds in different cloud regions, you could create multiple monitoring groups. For each group, select the corresponding region in scope configuration.
Example:
For South East Regions
- Monitoring Group Name: ap-southeast-alerts
- Scope: Include Region ap-southeast-1
- Notification Configuration: Send notification to slack channel: ap-southeast-alerts
For other regions
- Monitoring Group Name: Others-alerts
- Scope: Exclude Region ap-southeast-1
- Notification Configuration: Send notification to slack channel: other-regions-alerts
